Title
CVE-2022-35414 – QEMU 4.1.50 through QEMU 7.0.0 – address_space_translate_for_iotlb allows a guest user to crash a host resulting in a denial of service.
CVE ID
CVE-2022-35414
CVSS Score
N/A
Internal IDs
SICK-2022-113
Vendor
QEMU Project
Product
QEMU
Product Versions
QEMU version 4.1.50 through 7.0.0
Vulnerability Details
A vulnerability in qemu-system-aarch64 in QEMU 4.1.50 through QEMU 7.0.0 allows a guest OS to crash a host when a guess attempts to access an unmapped IOMMU. An attacker can crash and potentially execute arbitrary code as a QEMU guest. An uninitialized local variable in cputlb tlb_set_page_with_attrs causes a SIGSEGV in io_readx/io_writex via address_space_translate_for_iotlb when a CPU accesses an unmapped IOMMU via memory_region_register_iommu_notifier.
Vendor Response
https://gitlab.com/qemu-project/qemu/-/issues/1065
https://www.mail-archive.com/qemu-devel@nongnu.org/msg895266.html
https://gitlab.com/qemu-project/qemu/-/commit/549d4005874f602e957b07459949ae514ea96f20
Proof of Concept
Attempted to run varying imx6 kernels on qemu-system-aarch64 & qemu-system-arm.
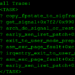
git clone https://github.com/ryzenlover/remarkable-mfgtools.git
# qemu-system-aarch64 -machine virt -cpu cortex-a57 \
# -device virtio-net-device,netdev=net0 -netdev user,id=net0 \
# -m 512 \
# -bios qemu-u-boot-bcm-2xxx-rpi4.bin \
# -device virtio-gpu-pci -serial stdio \
# -device qemu-xhci -device usb-tablet -device usb-kbd \
# -drive id=disk0,file=boot-image-qemu.hddimg,if=none,format=raw -device virtio-blk-device,drive=disk0
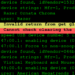
Jul 04 11:10:00.883873 hostname kernel: qemu-system-aar[191949]: segfault at a0 ip 000056298699d0bb sp 00007fe2bb9fde30 error 4 in qemu-system-aarch64[5629863bc000+97c000]
Jul 04 11:10:00.883965 hostname kernel: Code: 48 89 06 c7 46 08 01 00 00 00 44 89 66 20 0f 11 46 10 e8 b8 fc ff ff 48 8b 74 24 30 eb 53 90 48 8b 6c 24 28 0f 1f 00 48 89 ca <48> 8b 89 a0 00 00 00 48 85 c9 75 f1 80 7a 30 00 0f 84 9f 00 00 00Disclosure Timeline
- 2022-06-06 – Researcher discovers vulnerability
- 2022-07-04 – Researcher encounters vulnerability
Links
https://gitlab.com/qemu-project/qemu/-/issues/1065
https://github.com/sickcodes/security/blob/master/advisories/SICK-2022-113.md
https://sick.codes/sick-2022-113
https://github.com/qemu/qemu/blob/f200ff158d5abcb974a6b597a962b6b2fbea2b06/softmmu/physmem.c
https://github.com/qemu/qemu/blob/v7.0.0/include/exec/cpu-all.h#L145-L148
https://github.com/qemu/qemu/commit/418ade7849ce7641c0f7333718caf5091a02fd4c
https://www.mail-archive.com/qemu-devel@nongnu.org/msg895266.html
Researchers
- Trung Nguyen https://gitlab.com/TrungNguyen1909
- Sick Codes https://github.com/sickcodes || https://twitter.com/sickcodes
CVE Links
https://sick.codes/sick-2022-113


Comments 1