Title
Exposure of Sensitive Information to an Unauthorized Actor – Brave Browser Potentially Logs The Last Time A Tor Window Was Used.
CVE ID
CVE-2020-8276
CVSS Score
5.5
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N
Internal ID
SICK-2020-013
Vendor
Brave Software, Inc.
Product
Brave
Product Version:
1.18.27 and below.
Fixed in 1.18.34
Vulnerability Details
A vulnerability in the Brave Browser allows an attacker to view the last time a Tor session was used in incognito mode. A local, on-disk attacker could read the Brave Browser’s “Local State” json file and identify the last time a Tor session was used, affecting the confidentiality of a user’s Tor session.
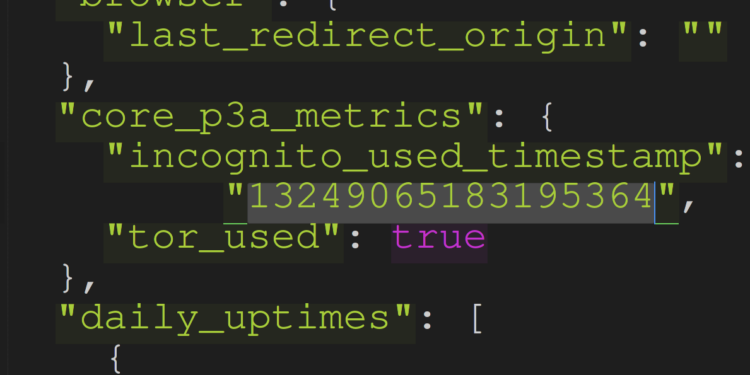
For example, the “Local State” file of a user who has recently used a Tor session would list a key value pair with a timestamp as accurate as “13248493693576042”. This allows an attacker to fingerprint, or prove beyond reasonable doubt, that a user was using Tor at that very specific moment in time.
Vendor Response
Fixed in 1.18.34 Brave Nightly Build, see Pull Request 7010
Disclosure Timeline
- 2020-10-30 – Researcher discovers vulnerability, when updating to latest Brave
- 2020-10-30 – CVE Requested
- 2020-11-02 – Researcher notifies vendor via email
- 2020-11-02 – Vendor confirms security concern and request submission through HackerOne
- 2020-11-02 – Researcher submits vulnerability via HackerOne
- 2020-11-02 – Vendor patches vulnerability
- 2020-11-04 – Vendor releases patch in Nightly Build
- 2020-11-04 – Public disclosure via HackerOne Report #1024668
- 2020-11-04 – CVE assigned CVE-2020-8276
Credits
@sickcodes – https://twitter.com/sickcodes Researcher discovery & report.
@bcrypt – https://twitter.com/bcrypt Brave Browser security team correspondent.
Links
https://hackerone.com/reports/1024668
https://github.com/sickcodes/security/blob/master/advisories/SICK-2020-013.md
https://sick.codes/SICK-2020-013
https://brave.com/new-onion-service
https://github.com/brave/brave-core/pull/7010
PoC
Open Brave Browser in incognito mode with Tor.
Close Brave browser, and view ~/.config/BraveSoftware/Brave-Browser/Local State
jq '.core_p3a_metrics' < ~/.config/BraveSoftware/Brave-Browser/Local\ State
{ "incognito_used_timestamp": "13248495136836403", "tor_used": true }
The above timestamp is permanent until overwritten, by another Tor session.
The tor_used Boolean refers to whether or not a Tor session has ever been used in Brave Browser, hence the term “potentially” in the report title.
Other metrics related to Tor in Local State:
"last_used": "Tor Profile", "metrics": { "next_bucket_index": 2 },
"core_p3a_metrics": { "incognito_used_timestamp": "13248493693576042", "tor_used": true },
"Brave.Core.TorEverUsed": { "sent": false, "timestamp": 0.0, "value": "0" },
"tor": { "tor_disabled": false },
Proof that tor_used Bool only refers to whether has ever used Tor:
-
- Open icognito with Tor:
jq '.core_p3a_metrics' < ~/.config/BraveSoftware/Brave-Browser/Local\ State
{ "incognito_used_timestamp": "13249022400646476", "tor_used": true }
-
- Open icognito without Tor:
jq '.core_p3a_metrics' < ~/.config/BraveSoftware/Brave-Browser/Local\ State
{ "incognito_used_timestamp": "13249022400646476", "tor_used": true }