This week, a cryptographically signed message using Hal Finney’s key surfaced. It was provided to Martin Shkreli. Martin followed his first post up with more questions, rather than answers:
https://martinshkreli.substack.com/p/new-hal-finney-signed-message-is
Currently there are a few possible reasons why someone can sign a message as Hal Finney: either someone has the late Hal Finney’s private key, which is understandable as his estate continues.
Or, he may have signed the message before he died.
Or, most likely, someone is trying to prove something (using the real private key, too).
Evan Ratliff also has signed messages, from someone who can sign them. Evan published a book on Paul Le Roux. I DM’ed him the latest unsealed court documents below, and we had a discussion will be outlined below: https://www.nytimes.com/2019/03/05/books/review/mastermind-evan-ratliff-paul-le-roux.html
Last week, the US Supreme Court made a significant decision to hear a case involving Adam Samia, a 48-year-old man who was convicted in 2018 for his involvement in the murder of Filipino real estate agent, Catherine Lee.
https://www.reuters.com/legal/us-supreme-court-review-murder-for-hire-conviction-2022-12-13
Samia was charged alongside former US Army sergeant Joseph Hunter and another North Carolina man, Carl David Stillwell, in relation to the crime. This case has garnered attention due to the high-profile nature of the defendants and the severity of the charges.”
And, because Paul Le Roux has testified against all of them.
How did Paul arrive in federal custody?
Crime.
Paul is a genius.
He has been doing cryptography for 30 years.
You can download Paul’s PGP key, from 1998.
Paul’s first important software project was E4M; Encryption for the Masses.
He uses the MIT license: http://cyberside.planet.ee/truecrypt/License-E4M.TXT
License agreement for Encryption for the Masses.
Copyright (C) 1998-2000 Paul Le Roux. All Rights Reserved.
This product can be copied and distributed free of charge, including
source code.Paul’s PGP key from the the year 2000.
https://web.archive.org/web/20010215003154fw_/http://www.e4m.net/pgp.asc
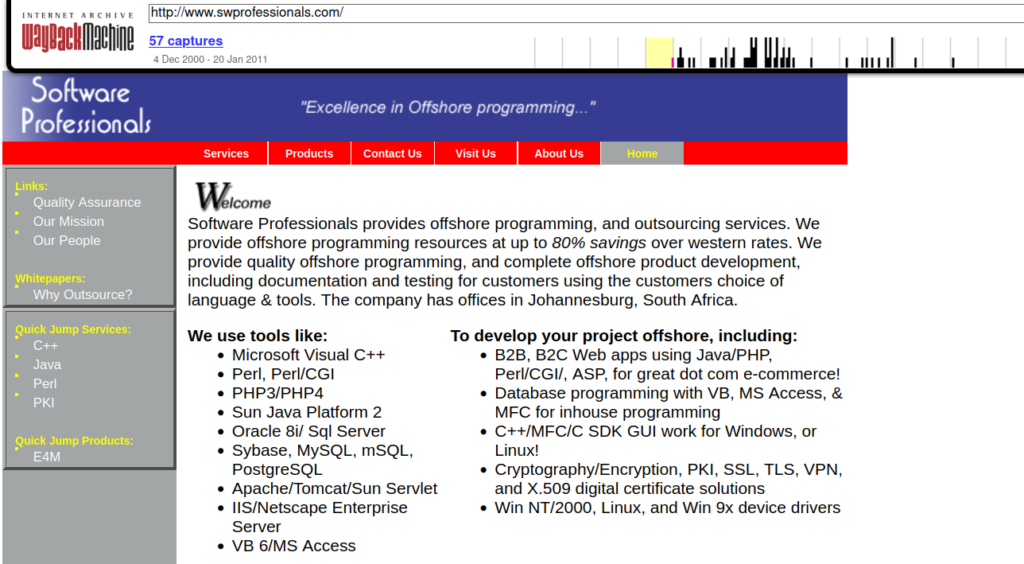
The key was issued in 1998 and the email ID is: info@swprofessionals.com
That email, “info@swprofessionals.com”, is mentioned in a forum post:
https://www.pcreview.co.uk/threads/truecrypt-1-0-released.1967957/
In the forum post from 2004, Paul was accused of publishing code that he had used previously while employed at SecurStar.
TrueCrypt is based on (and might be considered a sequel to) a discontinued product called Encryption for the Masses (E4M) by Paul Le Roux.
However, “SecurStar GmbH is a German computer security company founded by Wilfried Hafner in 2001, from the fusion of ScramDisk Inc., Software Professionals Ltd., and Telstar Industries.” Interestingly, Wilfried Hafner, is not a nobody, Hafner was in jail in 1997. He was, a hacker, named “Luzifer”.
https://www.phrack.com/phrack/50/P50-03
Stirring the pot, Wilfried Hafner, apparently , was jailed
License confusion:
http://www.mobileread.mobi/forums/showthread.php?t=1275
https://web.archive.org/web/20020331060618/https://www.phrack.com/phrack/50/P50-03
SecurStar’s Drivecrypt was sold to some pretty important businesses, as well as Governments too.
According to the Phrack post:
WHAT HE DID
===========
Luzifer set up some overseas partylines in the Dominican Republic,
Indonesia, The Philippines, and Israel. Some lines included live chat,
but most were just sex recordings. Then he used a local company PBX (a
Siemens Hicom 200 model), from his homeline, which was only "protected"
by a one digit code, to dialout to his partylines and his girlfriend in
Chile. He also was blueboxing (which the prosecution calls "C5-hacking")
from five lines simultaneously, mostly via China. To trick the partyline
provider and overseas telcos (who are aware of computer-generated calls)
he wrote a little program that would randomize aspects of the calls
(different calling intervals and different durations for the calls).What does this mean so far?
- Paul writes powerful encryption software.
- Paul has 3 decades of cryptography experience.
- Paul uses Windows.
- Paul likes MIT licenses.
- Paul’s email is pleroux@swprofessionals.com
Vistomail.com the domain was parked until 2009.
When the BTC paper was actually published, only a PLESK server was running on Vistomail.com (most likely, with mail).
https://web.archive.org/web/20090925040931/http://www.vistomail.com/
I submit to you, that Craig Wright, is right. He is “the person behind the moniker Satoshi Nakamoto.”
https://medium.com/@craig_10243/evidence-and-law-f8f10001efa5
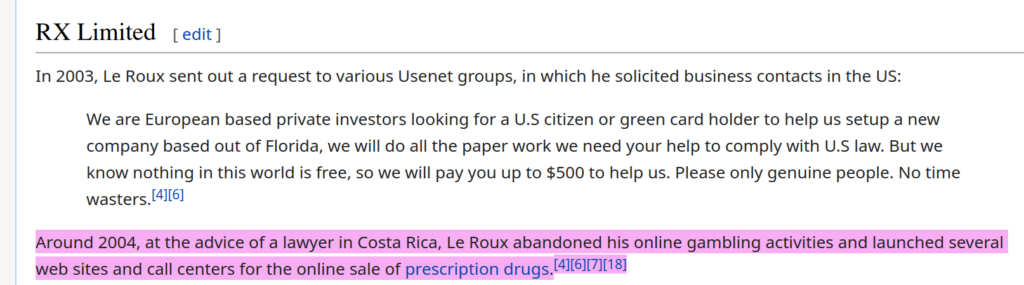
Craig and Paul have met. They were both involved, at some point in time, with online gambling in Costa Rica.
Unsealing Court Documents
Craig Wright in court:
https://www.courtlistener.com/docket/6309656/558/kleiman-v-wright/
Kleiman v. Wright
Sealed Document — Document #558
District Court, S.D. Florida
Docket Number: 9:18-cv-80176
Date Filed: June 2nd, 2020
Uploaded: June 15th, 2020
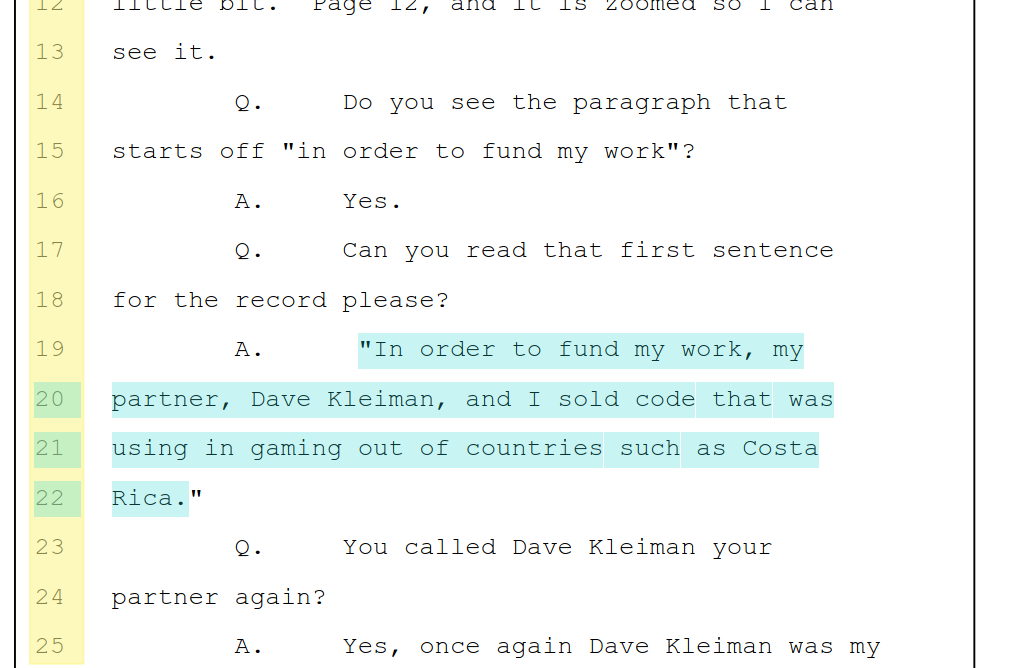
And Paul:
The Missing Link: Docket Entry 556

Smoking guns come out in Court.
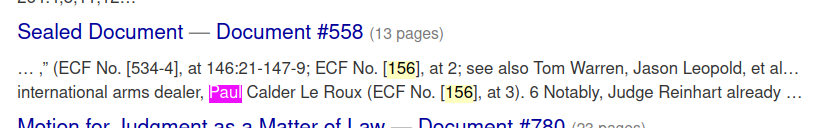
https://www.courtlistener.com/docket/6309656/558/kleiman-v-wright/
Craig Wright, in court filing 156 also describes Craig and Paul’s relationship.

In the following redacted document, the following page was not fully redacted:

https://medium.com/@fbonomi/paul-le-roux-has-nothing-to-do-with-bitcoin-f534890430db


Given the footnote is about Paul, would it be odd to assume the following?
Attempt to reverse the redactions:
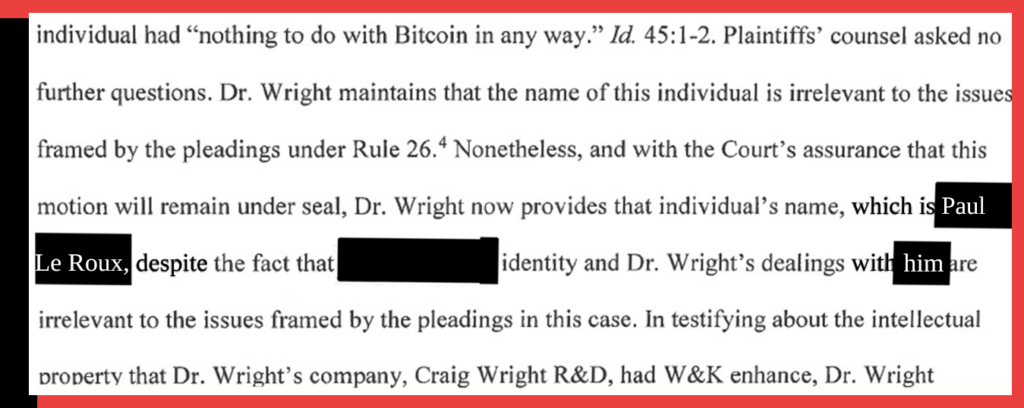
Speculation, but this feels oddly close.
Overlay of Times New Roman, potentially providing what’s under the redactions:







Just stumbled upon your research. There are some big flaws in it but the other parts are very interesting:
https://sick.codes/wp-content/uploads/2022/12/Screenshot_2022-12-16_14-47-35.png
-> The person who wrote Satoshi’s Vision: The Art of Bitcoin -> Paul Democritou
has nothing to do with Paul Le Roux and basically used Slack messages CSW wrote to his MetaNet audience and packaged it into a book. So you misinterpreted there.
https://martinshkreli.substack.com/p/new-hal-finney-signed-message-is
-> I think this has been debunked in various ways, so no direct connection either
The parts in court with CSW talking about LeRoux seem correct. He also talked about Gareth Williams but the connection is iffy. At one point (I think) he claimed a 3way phone call with Dave Kleiman and (Gareth Williams), but at that point Williams was already dead.
Either way, I liked the work you have done. If you want to talk further for example via twitter or some other way, let me know.
Best,
F
Damn, when he mentioned the book and Paul, I thought he was talking about the big dog xD
Go to hoddcoin.com and download the only Court Order in the COPA v Dr. Craig Wright London case, that Paul Le Roux being Satoshi Nakamoto was raised.
COPA v. Dr.Craig Steven Wright case in London. The picture of the whole truth raised in a minor court order. The true Satoshi Nakamoto could have been outed in Court 26. But destiny has other plans.
hoddcoin.com
Paul Calder Le Roux is 100% Satoshi Nakamoto. All the facts fit like a glove.