Nobody uses a Hackintosh to play Fruit Ninja, create iMovies, or write songs on Garage Band.
Researchers use Hackintosh to conduct security research on tasks that require a real (KVM) Mac.
Developers use it to automate releases of their Applications, minimizing human error, and maximizing end-user security.
If you want to get join the Apple Bug Bounty program, you can get started using Docker-OSX.
How to Hackintosh in good-faith.
In December 2019, Apple opened up the Apple Security Bounty program, to everyone. That means everyone.
Creating and conducting security research under the terms of the Apple Security Bounty program is permitted.
Apple explicitly permits that,
“A participant in the Apple Security Bounty program (“ASB Participant”) will not be deemed to be in breach of applicable Apple license provisions which provide that a user of Apple software may not copy, decompile, reverse engineer, disassemble, attempt to derive the source code of, decrypt, modify, or create derivative works of such Apple software, for in scope actions performed by that ASB Participant where all of the following are met:
– “The actions were performed during good-faith security research, which was — or was intended to be — responsibly reported to Apple;
– “The actions were performed strictly during participation in the Apple Security Bounty program; and
– “Neither the actions nor the ASB Participants have otherwise violated these policies such as violating legal requirements 1, 2, and 3, above.”
Link to the terms, if you want to read them all (very short read)
There is no grey area there, whatsoever.
Apple explicitly states that they do not consider a violation of the EULA, under the terms of their program, provided that you participate in the program in good-faith, that you do not disrupt Apple services, and that you do not access anyone else’s data.
But most importantly, if you do discover vulnerabilities, you must report them to Apple.
You must abide by the rules of the program, or you are in breach of their End User License Agreement (EULA).
While the EULA is not the Law, you would have accepted the EULA when you install MacOS.
The question remains…
Do you need Apple hardware to participate in the Apple Bug Bounty program?
No! Apple has a large scope, which includes their website, their servers, their software, and their hardware.
Obviously, you will not be able to find physical hardware bugs without the device, but there are plenty of firmware and software bugs that Apple is very interested in you finding.
Does Apple care?
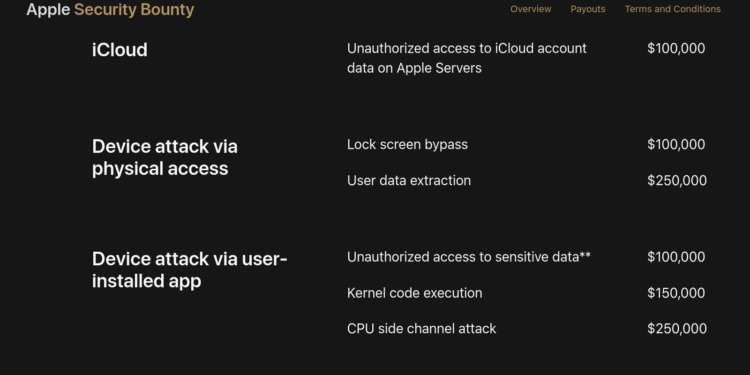
Yes! Apple welcomes security research. If you do find valid security bugs, Apple will pay upwards of $100,000 for valid research.
If you discover a bug using a KVM mac, and report it to Apple, please reach out and I will add you to our Docker-OSX project Hall of Fame
Are you sure?
I do not own a Mac.
However, I own several iPhones.
They are all jailbroken using unc0ver or checkra1n.
I jailbroke my iPhone 12 using Docker-OSX, and previously I used OSX-KVM to jailbreak my iPhone 11.
In order to conduct research on those two devices, I may have violated the MacOS desktop EULA.
I have every intention of reporting bugs to Apple.
Apple is more than aware of the amount of security bugs that have been discovered through the use of jailbroken iPhones.
Docker-OSX
https://github.com/sickcodes/Docker-OSX/
The project is made by devs, for devs. It’s GPLv3+, so you are free to use the code in the project in any way. You are even permitted to create proprietary software with Docker-OSX. You are not forced to release the source code of your proprietary software because we don’t use the AGPL license.
If you need an example, consider gcc, the GNU project C and C++ compiler.
https://www.gnu.org/licenses/gpl-faq.html#CanIUseGPLToolsForNF
“Can I use GPL-covered editors such as GNU Emacs to develop nonfree programs? Can I use GPL-covered tools such as GCC to compile them? (#CanIUseGPLToolsForNF)”
Yes, because the copyright on the editors and tools does not cover the code you write. Using them does not place any restrictions, legally, on the license you use for your code.
As a security researcher, a hacker, and a developer, I love doing what I do.
I wake up every day, develop software for my private clients, contribute to Free Software, as well as Open Source, and participate in security research.
You can find me on twitter: https://twitter.com/sickcodes
And all these places:
https://hackerone.com/sickcodes
https://bugcrowd.com/sickcodes
https://hub.docker.com/r/sickcodes
All product and company names are trademarks™ or registered® trademarks of their respective holders. Use of them in this news post does not imply any affiliation with or endorsement by them.

Comments 2