A PGP key is an encryption key with two main parts:
- Private Key
- Public Key
The owner of the key pair is the only individual that should have access to the Private Key, at any time.
A Public Key can be posted anywhere.
When someone wants to send you a secret message, or file, they can use your public key to generate cipher text.
Only the Private key can decrypt that cypher text.
GNU Privacy Guard (GPG) can be used to do PGP activities (Pretty Good Privacy).
gpg
gpg is most likely already installed on your distro. It should come with homebrew on Mac, or install with brew install gnupg.
Fast Way To Generate A Secure Key
# make a key pair, follow the prompts gpg --gen-key # export the public key to txt gpg --output public-key.txt --export --armor 'johndoe@localhost'
Long Way (Bigger Key Size 4096, More Secure)
Generate a full key (public and private).
gpg --full-gen-key
Choose RSA + RSA
RSA and RSA
Choose a keysize of 4096 bits
4096
Choose an expiry time of two years
2y
Enter your name, or alias, and email address.
You will be asked to set a passphrase.
This is a password for the private key.
So, even if someone has the private key, they still need to password to use it.
You’ll need to enter this password anytime you want to decrypt messages.
Make a big password, but one that you will remember.
If you forget this passphrase, it is virtually impossible to use your keys again.
A typical key lifespan is two years. It is not recommended to make a key that will never expire.
If the password is too small, someone can brute force entry into the private key (they still need the key in the first place).
Example Output:
gpg: key 7BB47A69CE91569C marked as ultimately trusted gpg: revocation certificate stored as '~/.gnupg/openpgp-revocs.d/4FFF1CFF1D52EF7D86F82C277BB47A69CE91569C.rev' public and secret key created and signed. pub rsa4096 2020-12-17 [SC] [expires: 2022-12-17] 4FFF1CFF1D52EF7D86F82C277BB47A69CE91569C uid Jane Doe sub rsa4096 2020-12-17 [E] [expires: 2022-12-17]
This key was named on the local machine as
7BB47A69CE91569C
For the above key, the public fingerprint is
4FFF1CFF1D52EF7D86F82C277BB47A69CE91569C
The public fingerprint is sometimes stored like this:
4FFF 1CFF 1D52 EF7D 86F8 2C27 7BB4 7A69 CE91 569C
The fingerprint is not used to sign messages, you need the entire public key:
Exporting The Public Key
Show your keys:
gpg --list-keys
You can refer to the key you just made in multiple ways:
# these are all the same # email gpg --output public-key.txt --export --armor janedoe@localhost # name/id gpg --output public-key.txt --export --armor 7BB47A69CE91569C # public signature gpg --output public-key.txt --export --armor 4FFF1CFF1D52EF7D86F82C277BB47A69CE91569C
This will generate a txt file with a Public Key!
gpg --output public-key.txt --export --armor 'johndoe@localhost' cat ./public-key.txt
Example output:
-----BEGIN PGP PUBLIC KEY BLOCK----- mQGNBF/bBAIBDADpwGYV5wiI/i6Ov+EuTm/AhEX/4DgXEIyisKYVFfhAsrgMNRE4 M4yBPyC8ewsGiY0jmlU/Zy2KM9fiFrYYKpU26/otpschq0430r2Fygopfrv+NE7L ... ... ... SSv/L0c8C0W6QSzds7jVbnhFdgHwZgQqPCb5EpVi+H3ecQ5lZ4c/2riBj7uQ6Rfl VdKpulxA1dFth9nwKaVeWDcT+Fg= =zgkU -----END PGP PUBLIC KEY BLOCK-----
Test Your PGP Keys
I use GPG Crypter to encrypt/decrypt messages.
https://sourceforge.net/projects/gpg-crypter/
https://www.archlinux.org/packages/community/x86_64/gpg-crypter/
But if you want to test the key out, you can encrypt messages online https://8gwifi.org/pgpencdec.jsp
You can paste the public key anywhere you want. Do not paste your private key in a website, that would be ridiculous.
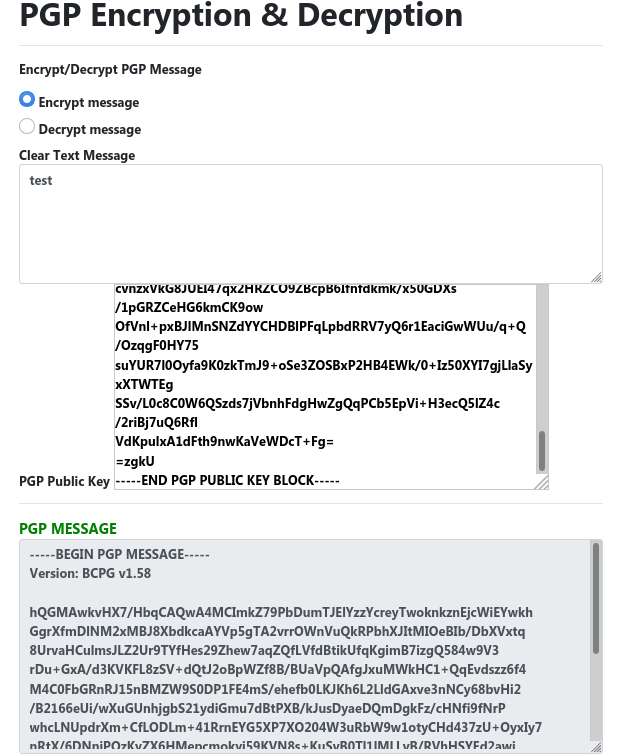
Using other public keys to encrypt messages for them to read (and only them)
You can import someone’s Public Key into gpg and it will show up inside GPG crypter.
You can import a Public Key from a txt file or standard input:
Just save the public key block into a text file, and import it.
gpg --import public-key.txt
gpg will find the start and end of the public key.
Or you can use standard input!
gpg --import <<'EOF' -----BEGIN PGP PUBLIC KEY BLOCK----- mQGNBF/bBAIBDADpwGYV5wiI/i6Ov+EuTm/AhEX/4DgXEIyisKYVFfhAsrgMNRE4 M4yBPyC8ewsGiY0jmlU/Zy2KM9fiFrYYKpU26/otpschq0430r2Fygopfrv+NE7L ... ... ... suYUR7l0Oyfa9K0zkTmJ9+oSe3ZOSBxP2HB4EWk/0+Iz50XYI7gjLlaSyxXTWTEg SSv/L0c8C0W6QSzds7jVbnhFdgHwZgQqPCb5EpVi+H3ecQ5lZ4c/2riBj7uQ6Rfl VdKpulxA1dFth9nwKaVeWDcT+Fg= =zgkU -----END PGP PUBLIC KEY BLOCK----- EOF
Then you will see that key inside GPG Crypter.
You will be able to encrypt messages, but will not be able to decrypt messages using just someone’s public key.
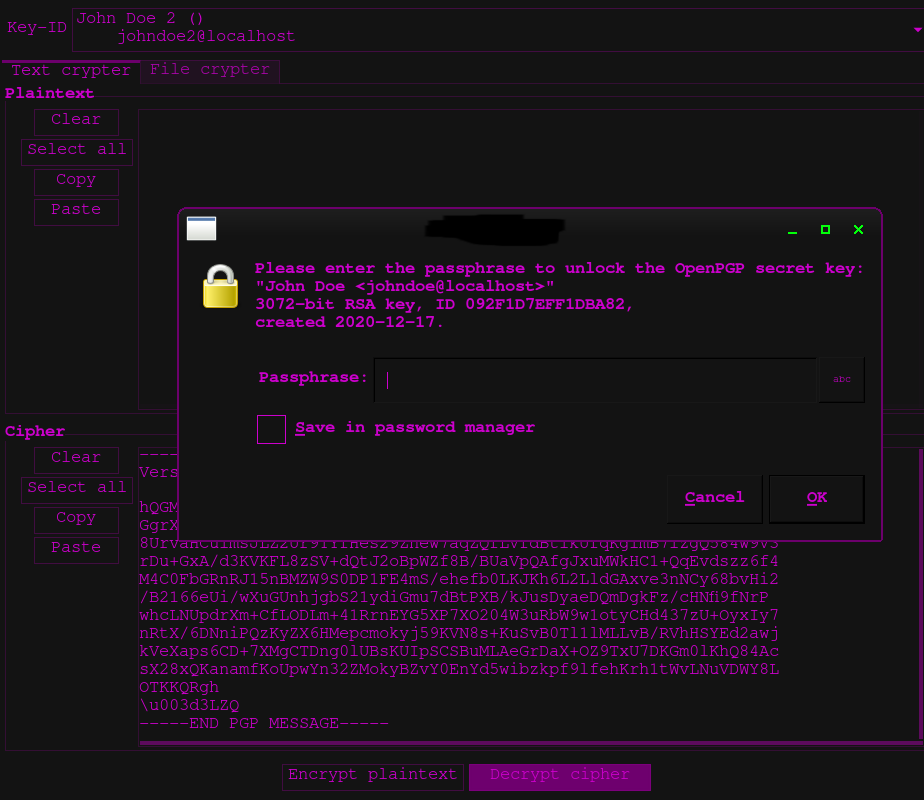
Decrypt a PGP message
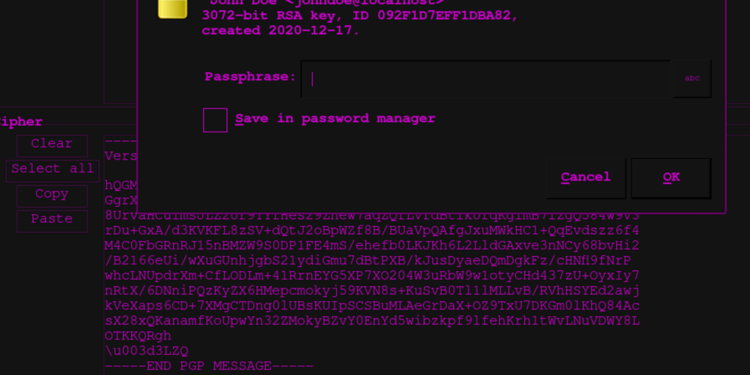
Simply paste the cipher text into GPG Crypter, choose your key from the dropdown, and click decrypt text.
You will have to enter the password!