Follow me on Twitter @sickcodes: https://twitter.com/sickcodes
This research began in early September and I’ve been waiting on several confirmations to publish said investigation.
End-users include very large corporations and Government entities in dozens of countries. Given the recent supply-chain attacks, it only recently exacerbated my professional opinion regarding this research.
The software I discovered this vulnerability in is kind of like Git, but for modelling things.
Link to the CVE: https://sick.codes/sick-2020-002/
EDIT March 2021
Fixes have been published by 3DS at the following links:
https://community.nomagic.com/finding-and-fixing-wrong-file-permission-twc-installation-t7165.html
It’s a self-hosted solution, much like Gitlab, however this software is used in enterprise settings for state-of-the-art 3D modelling.
High profile users of the software include:
- NASA
- Raytheon
- Boeing
- Airbus
- Lockheed Martin
In fact, the it was probably used during F-35 development: https://www.aerospacemanufacturinganddesign.com/article/aerospace-manufacturing-design-f35-dassault-031511-amd/.
The main use case of the software is the ability for modellers to remotely collaborate on highly proprietary projects such as:
- Aerospace engines
- Missiles & weapons systems
- Telescopes
- Submarines
- Medical products
- Satellites
… and more!
I’m publishing this research a bit after day 90, which is the first time I’ve waitied this long to release a vulnerability.
I post research very often, so if you’re interested in this, you can follow me on Twitter @sickcodes: https://twitter.com/sickcodes
As of time of writing, there is a published patch available on the vendor’s website that myself (Sick.Codes) and the vendor collaborated on: https://community.nomagic.com/finding-and-fixing-wrong-file-permission-twc-installation-t7165.html
What initially appeared to be a rather benign vulnerability, actually turned out to be much more penetrating than initially thought…
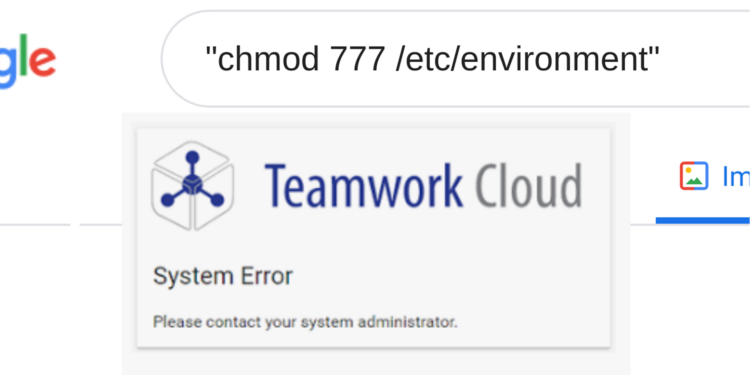
Using Google to find vulnerabilities.
On 2020-09-09, I was searching on Google for stupidly vulnerable code.
The search term that I used to find this vulnerability was (no joke):
"chmod 777 /etc/environment"
For those who are unaware what this command would do, /etc/environment is a very special file in GNU/Linux. It is the same as ~/.bashrc or ~/.profile, but for the whole system. Shell code in that file is executed by all users, including root, when they log in, or when the system is rebooted.
Therefore, having full read/write access to the /etc/environment file essentially renders the system completely vulnerable to attack, namely local privilege escalation.
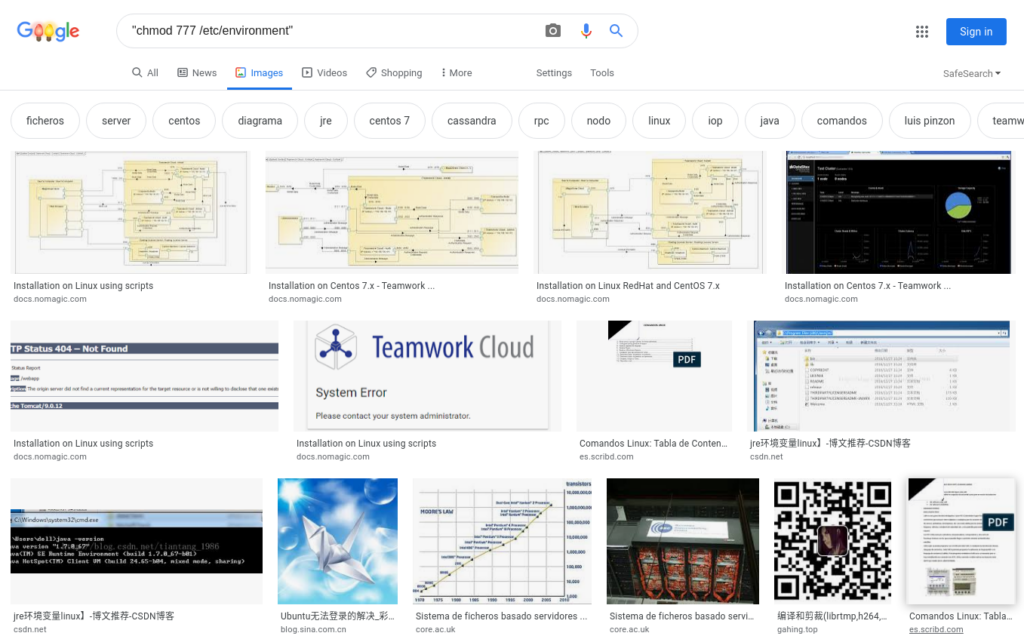
After hitting “Search” for the above term, I was immediately presented with documentation from a company called NoMagic. Like many readers, I had not heard of this company before.
If you don’t believe me, you can check the Google Images search below, it should still be in the cache. Here are the first 6 results anyway, and they are all from NoMagic, Inc.:
While the actual documentation has since been removed, you can view a copy of the shell script here: https://github.com/sickcodes/security/blob/master/etc/CVE-2020-25507_install_twc19_centos7.sh and an archive of the actual instructions here or a mirrored archive here.
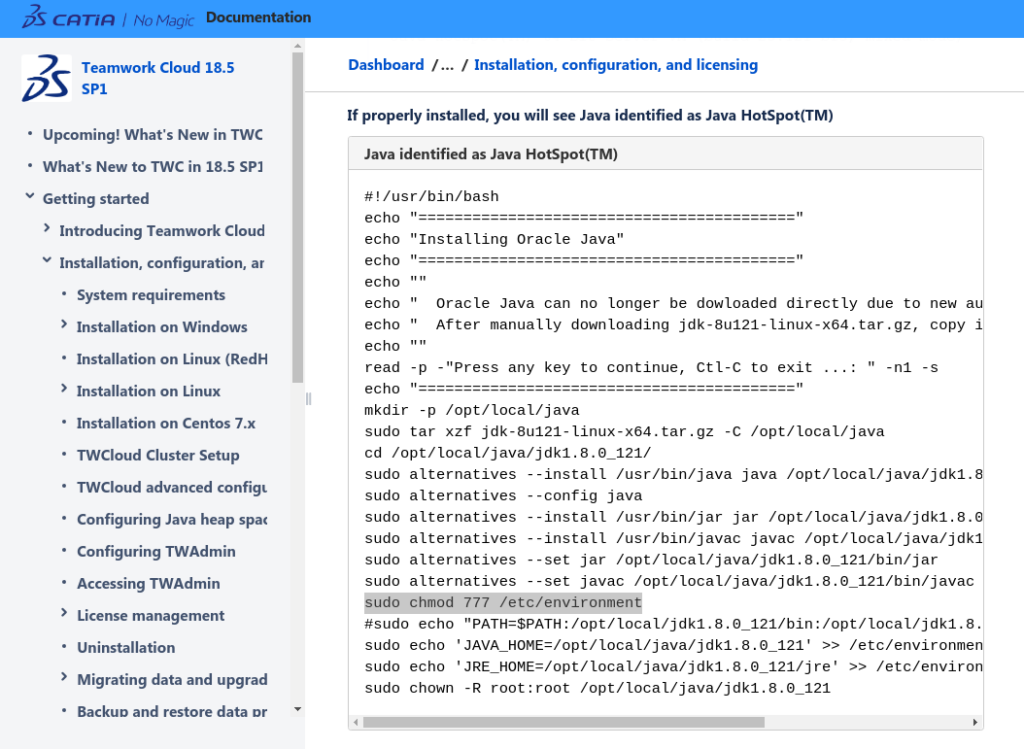
Executing this command during installation completely negates any permission granularity.
Moreover, any sub-user, such as a junior designer, who is given remote access to design 3D models, can subsequently take over the entire server.
Instead of being able to work on just one project on the Teamwork Cloud server, they can download ALL of them.
At the time of discovery, back in early September, I assumed that the vendor was a simple tech company in Allen, Texas.
Nonetheless, I was in the mood for an easy CVE, so I requested a CVE from MITRE. Link to CVE-2020-25507
Bizarre Support Systems
I drafted a small support ticket, then visited the support page: https://www.nomagic.com/support/general-support
My excitement was short-live.
NoMagic has an extensive 3 page Customer Support Service Policy, which I will entertain you with:
When submitting a Case, Customer will also propose an urgency level according to the impact of the Case regarding Customer’s day-to-day operation. Four levels of urgency are available. - Urgent: Customer is unable to use the Licensed Programs and have severe/critical impacts on operations, and no Workaround exists. - High: Customer is able to use the Licensed Programs but operations are severely restricted by the incident. A Workaround exists. - Medium: Customer can use the Licensed Programs with some restrictions on one or several functions. These restrictions, however, do not have a severe impact on Customer’s operations. - Low: The Case causes little or no impact to Customer’s operations.
That’s funny, I don’t remember signing into an agreement just to send a support ticket!
Second to that, you must register on the website to submit a support ticket.
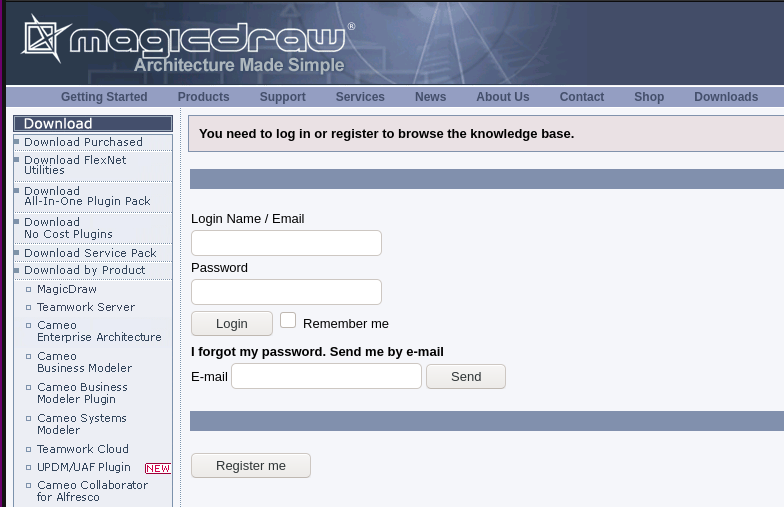
Thirdly, at the time of discovery (and right now), the support system was a broken link: http://knowledgebase.nomagic.com/.
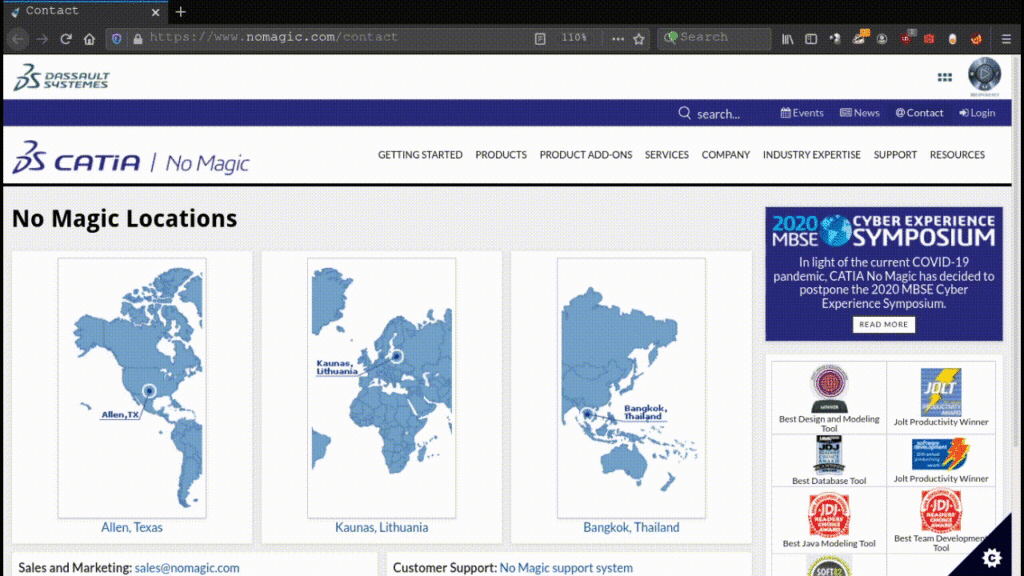
Since I didn’t have time to waste at that moment, I planned to revisit the support portal when it was alive again, or when the CVE was assigned, whichever came first.
Big companies and forgotten vulnerabilities
A few weeks later, on 2020-09-22, I returned to NoMagic’s website and noticed that the vulnerable documentation was still live on their website.
Having not heard from MITRE yet, I decided to return again later. Given this is unpaid Security Research (3DS does not have a bounty program), I didn’t have time to jump through hoops.
A few more weeks of customers using vulnerable installation scripts won’t hurt, right?
Then, about a month later on 2020-11-02, the CVE ID was finally assigned (Link to CVE-2020-25507).
This actually surprised me because I assumed MITRE just wasn’t interested in that software.
Little did I know, MITRE actually uses the NoMagic software!

Now that it had been assigned a CVE, it was now my responsibility to follow through with the research.
I proceeded to email NoMagic at a range of different email addresses:
sales@, security@, privacy@ & jobs@.
Unsurprisingly, the security email bounced, which is rarely a good sign.
Since I was not in the North American timezone at that moment, I decided to call NoMagic’s Asia office on the phone and prod the vulnerability along. Here is the phone call I had with NoMagic Asia:
After a very brief call, I forwarded the CVE request to salesasia@.
Big companies owned by even bigger companies
The next day, I finally worked out that NoMagic is actually owned by a very large parent company named Dassault Systèmes SE (3DS). 3DS appears to have purchased NoMagic back in June 2018.
As I had not heard from them yet, I began to wonder… What kind of company doesn’t respond to emails?
Why would a company not respond to sales emails? Do they not want to make any sales?
The answer is: A company that is owned by a larger company!
I didn’t know much about Dassault Systèmes, however, I definitely do now… 3DS is an enormous company. They are a Fortune 50 software company that specialize in 3D design.
The reason why NoMagic has still, to this day, not responded to any emails, pretty much explains the situation.
When 3DS purchased NoMagic, they inherited all the old code base.
However… they forgot to do something important… they forgot to audit the giant Pull Request!
In my professional opinion, I honestly couldn’t think of anything more ridiculous than:
>Buying a software company.
>Merging all of their code into your software suite.
>Forgetting to audit all the incoming code.
You’d think that when a multinational, high profile company with many, many clients, some of which are defense contractors for Governments all around the world, that they would at least spend a few days auditing the product that they bought?
For this reason, I would encourage readers who are faimiliar with this scenario, or who have been part of two companies merging before:
Would you merge unknown code into your code without vigorously testing it?
Without auditing the code base that you are inheriting, a company puts itself, and its loyal customers, at great risk.
New Cyber Attack vector 2021:
Make your SAAS so corporately buyable that it gets trojan-horsed into the true upstream target.
Moral of the story: audit code when two companies merge.
Bug bounty hunters: find companies with multiple intertwining products.
3DS Security Team gets an A+
Although it’s now very obvious to me that Dassault Systemes owns NoMagic, it wasn’t until I understood that did I know who to send the vulnerability report to.
Fortunately, once I realised who owned NoMagic, I checked the place I always check first for security contacts:
https://github.com/disclose/diodb/blob/master/program-list/program-list.json
That’s diodb, a crowd sourced bug bounty contacts database.
Most companies with security programs are in there and you can just Ctrl+F search through it.
Although I couldn’t find 3DS in there at the time, they’re in there now: https://github.com/disclose/diodb/commit/d0fb00475390f7de16a55ae8ed4b8046e06bcaaa
If you deal with a company and have had to dig to get their contact details, I recommend submitting a PR when you find a contact to https://github.com/disclose/diodb
Anyway, I went straight to 3DS’s vulnerability reporting page: https://www.3ds.com/vulnerability-reporting/
I sent them the report, writing that I had had trouble getting onto NoMagic.
Dassault Systemes were actually fantastic, they responded the very next day.
In fact, the timezones are messy, but I think they first responded in 30 minutes lol.
Sent: mercredi 4 novembre 2020 06:37: Replied: Nov 4, 2020, 07:05
@3DS Why don’t you put the link to the 3DS security page on NoMagic’s site?
Not only that, but once the right team had the info, they followed up on their Saturday night!
In my opinion, 3DS needs to merge the two support teams into one, given that the software has already been merged.
I kindly recommend that all vendors add security contact details to their site; I discovered this vulnerability back in early September and 3DS only received the report at the start of November, because the submission process wasn’t exactly optimized.
So what does the NoMagic software actually do?
NoMagic is part of a software suite by 3DS called CATIA, which is used by enterprise 3D modelling teams to work on products collaboratively, but also other stuff that I don’t know about, like business process modelling:
- Unified Modeling Language (UML)
- Business Process Model and Notation (BPMN)
- Systems Modelling Language (SysML)
- Unified Profile for DoDAF/MODAF (UPDM)
- Service-oriented architecture (SOA) Modeling Tools
NoMagic must make an exceptional product because their client list is not only impressive, it is practically the Forbes list!
MagicDraw Teamwork Server is the name of the software that allows more than one developer to work with the same model at the same time, and Teamwork Cloud is the upgraded version of Teamwork Server.
Who can exploit this vulnerability?
If the server is using native authentication, as in, normal Linux user accounts, then any user who has been provisioned an account, even if only temporary access, can effectively take complete control over the system.
I set up a CentOS7 test server, as per the installation scripts, and was subsequently instructed to connect to the system using SSH tunnel. Therefore, if the default sshd configurations are kept, then a user who can SSH into the server can also edit /etc/environment.
Althought it might appear that this Local Privilege Escalation exploit is not that important…
I encourage you to ask yourself:
What could possibly be stored on the self-hosted 3D modelling version control system for pretty much all of the world’s largest aeronatuical and defense engineering teams?
I think I know, but it would be on par with:
Maybe half of a decade’s top secret and highly confidential designs, plans, and business process models?
Who uses NoMagic?
As per the NoMagic website: https://www.nomagic.com/company/our-clients
| IT/Consulting | Defense |
|---|---|
| BEA Systems | Department of Defense |
| IBM | Canada National Defense |
| Saguaro Technology | U.S Army, Navy, Airforce |
| Trigent Software | Coast Guard |
| VERMEG | U.S Military Academy at West Point |
| Siemens | NAVAL Post Graduate School |
| Mitre Corp | Australia Submarine Corp |
| ORACLE/Sun Microsystems | Booz Allen Hamilton |
| Deloitte Consulting | Boeing |
| Wipro | Missile Defense Agency |
| Microsoft | BAE Electronic Systems |
| CSC | CACI |
| SAP | Northrop Grumman |
| EMC | Rockwell Collins |
| Red Hat | SPARTA |
| Tibco | Raytheon |
| Accenture | General Dynamics |
| Capgemini | L3 Communications |
| SAIC | B&W Pantex |
| PricewaterhouseCoopers | ITT |
| Gartner | NEWTEC |
| Mantech | |
| thyssenkrupp Marine Systems |
| Aerospace/Automotive | Government |
|---|---|
| Boeing | Australian Securities & Invest |
| DaimlerChrysler | SITA (State Information Technology Agency) |
| Lockheed Martin | State of New Jersey, Office of IT |
| LTU Lufttransport Unternehmen | NSA |
| Rolls Royce | Department of Energy |
| Porsche/VW | Sandia Labs |
| GM | JPL |
| Ford | NIST |
| NASA | GSA |
| Bombardier Inc. | U.S Forest Services |
| Nissan | CSE, Government of Canada |
| Toyota |
| Manufacturing/Electronics | Telecommunications, Transport, Logistics |
|---|---|
| Honeywell | Avaya |
| XEROX | Covad Communications |
| Nikon | DHL |
| John Deere | DNA Finland Oy |
| General Electric | Eurotel Praha |
| Hewlett-Packard | NEC |
| TRANE | Nortel |
| Samsung | Deutsche Telekom AG |
| Sony | British Telecom |
| LG | Ericsson |
| Alpine Electronics | FedEx |
| Nippon | Expeditors |
| Siemens AG | Maersk Data Defence |
| Mitsubishi Electric | Port Infolink B.V. |
| Samsung Electronics Research Institute | Salomon Automation |
| Research In Motion | Teligent AB |
| Convergys | Verizon Wireless |
| ABB | Reuters |
| Tyco Electronics | ATX Group |
| Sumisho | GE Transportation |
| Voltwerk Electronics | Birch Telecom |
| Motorola | Bouygues Telecom |
| Vodafone |
| Healthcare, Pharmaceuticals | Consumer Goods/Entertainment |
|---|---|
| Bear Creek Corporation | NuSkin |
| Electronic Healthcare Systems | Macy’s |
| LION bioscience AG | Chick-Fil-A |
| VSA GmbH | ESPN |
| Boston Scientific | Sony |
| GE Healthcare | Disney |
| Canada Health Infoway | Johnson & Johnson |
| Department of HHS | Ubisoft |
| Baxter Healthcare | Electronic Arts |
| Bayer Healthcare | |
| Pfizer Health Solutions | Red Hat |
| Cardinal Health |
| Oil/Energy | Education |
|---|---|
| DynMcDermott Petroleum | MIT |
| Shell Canada Limited | UC Berkley, San Diego |
| Duke Energy | Yale University |
| Shell Europe Oil Products | Purdue University |
| British Petroleum | British Columbia University |
| AESO, Canada | Indiana University |
| U.S. Department of Energy | U.S. Military Academy |
| GE Hitachi Nuclear Energy | The University of Texas |
| Schneider Electric | Johns Hopkins Univ |
| Mitsubishi Electric Co. | Georgia Tech |
| University of Waterloo (Ontario) |
| Financial Services | Financial Services |
|---|---|
| ACORD | Credit Suisse |
| Bancoval | Ford Credit |
| Banque COVEFI | GMAC BANK |
| Barclays Global Investors | Nykredit Data |
| Bloomberg | Prima-solutions |
| Citigroup | Textron Financial Corp |
| CitiMortgage | Thompson Financial |
| Generali | Fidelity Investments |
| Lincoln Financial | Pay Chex |
| HSBC | Prudential |
| XBRL | SWIFT |
| ADP | Fix Protocol |
| JP Morgan Chase |
Quick Links
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-25507
https://nvd.nist.gov/view/vuln/detail?vulnId=CVE-2020-25507
https://sick.codes/sick-2020-002/
https://github.com/sickcodes/security/blob/master/advisories/SICK-2020-002.md
https://community.nomagic.com/finding-and-fixing-wrong-file-permission-twc-installation-t7165.html
https://github.com/sickcodes/security/blob/master/etc/CVE-2020-25507_install_twc19_centos7.sh